MANCON
1M5 dynamically bypasses attempts to censor communications between decentralized applications in which 1M5 is used. It does so by maneuvering against blocks and attacks on the internet as well as outside of the internet. This maneuvering experiences varying levels of situational conditions called MANCON.
MANCON is an alert state signalling the maneuvering required to achieve the mission. It can change at any time in response to new conditions arising. Currently, the base MANCON recommended for a claimed jurisdiction is largely based on the Press Freedom Index. Soon, it will be based on autonomous ManCon nodes in each jurisdiction testing local networks providing ManCon recommendations to 1M5 peers.
End-users can at any time select the MANCON they feel they need to protect their privacy.
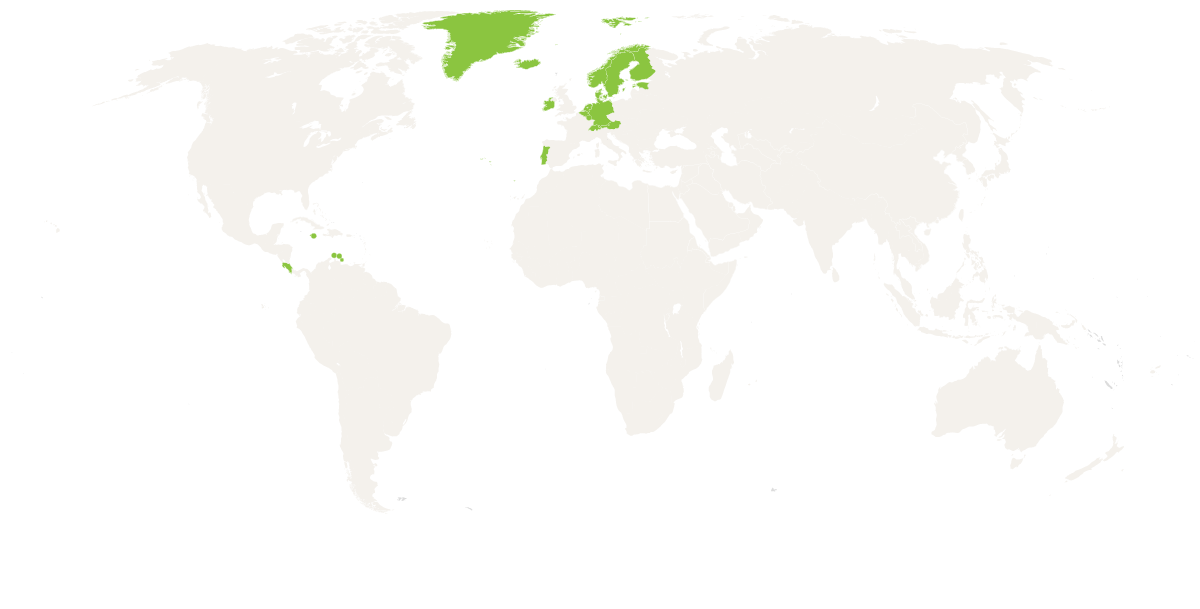
Open/normal SSL based communications with no expected censorship or privacy intrusion attempts is the norm.
- Web: I2P used for .i2p addresses and Tor for other web requests including .onion addresses. If that fails, it will be assumed that the site is down.
- P2P (Messenger): I2P used unless found to be blocked. Then Tor will be used as a tunnel to a peer that has I2P enabled. If Tor blocked, will ratchet up to non-internet (e.g. Bluetooth) for assistance.
- Expect latencies of 500 milliseconds to 2 seconds unless non-internet is needed.
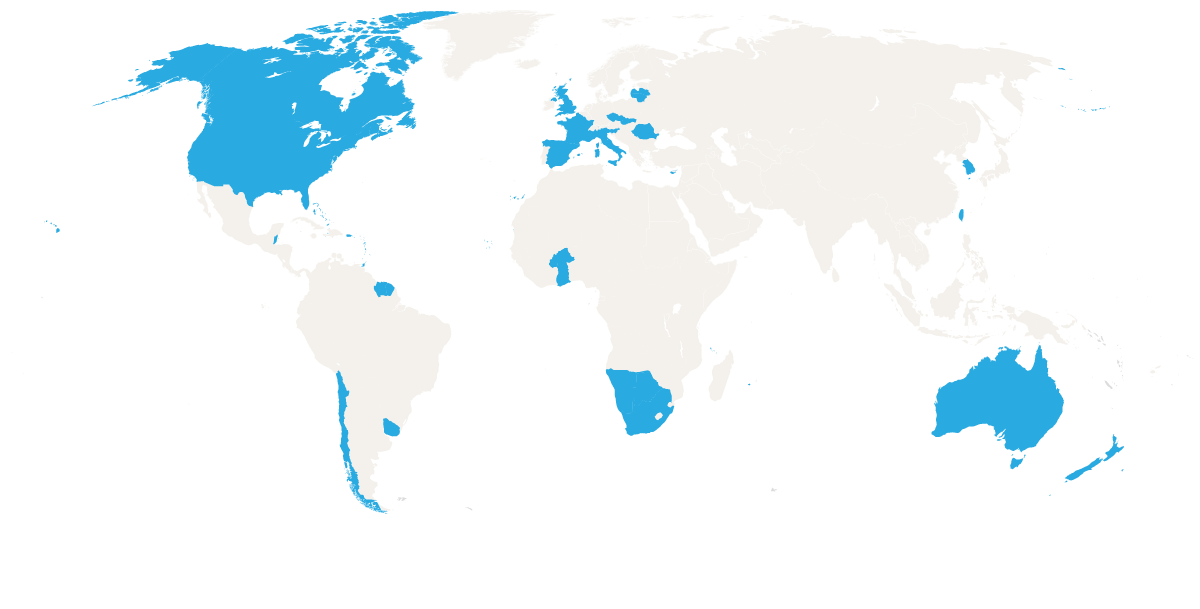
Normal censorship attempts by states on reading news (public web sites getting blocked, government shutdown of cloud cdn content). Many moving towards using Tor and/or VPNs although no fear of circumventing censorship attempts.
- Web: Unchanged unless Tor fails, then request will be forwarded to an I2P peer with Tor access to make the request returning the result directly back to the requesting peer. If those fail, it will be assumed that the site is down.
- P2P unchanged
- Expect latencies of 500 milliseconds to 4 seconds unless non-internet is needed.
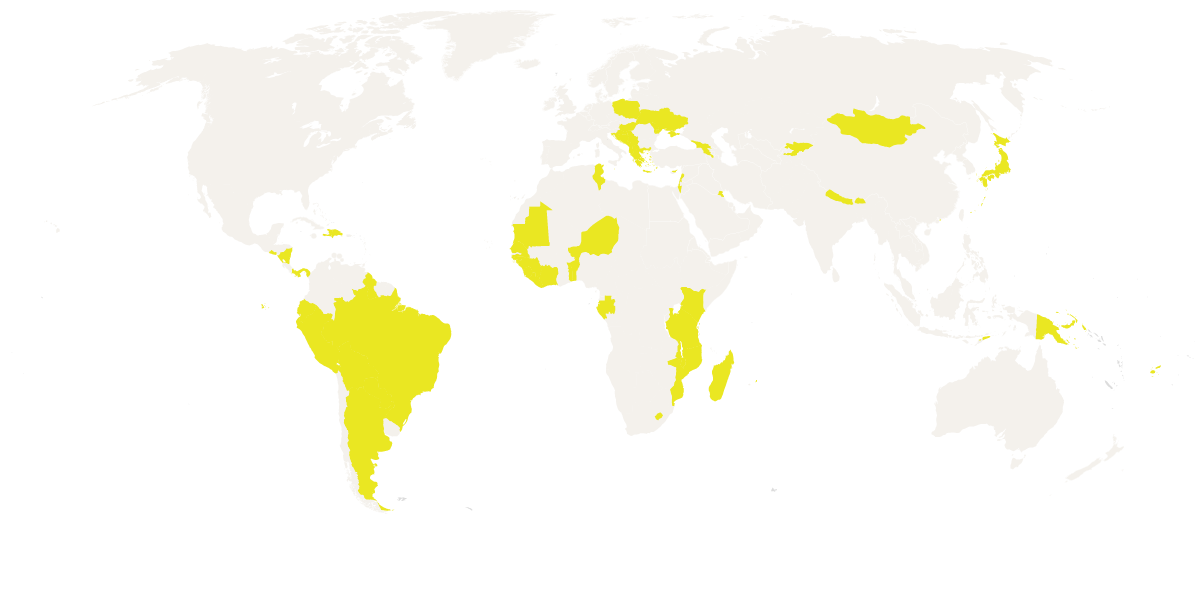
Tor and VPNs are beginning to get blocked. Many beginning to move to I2P. Some self-censorship likely. This is the default setting for 1M5.
- Web: will use an I2P peer that has access to Tor to make the request escalating to non-internet if necessary.
- P2P unchanged
- Expect latencies of 2-4 seconds unless non-internet is needed.
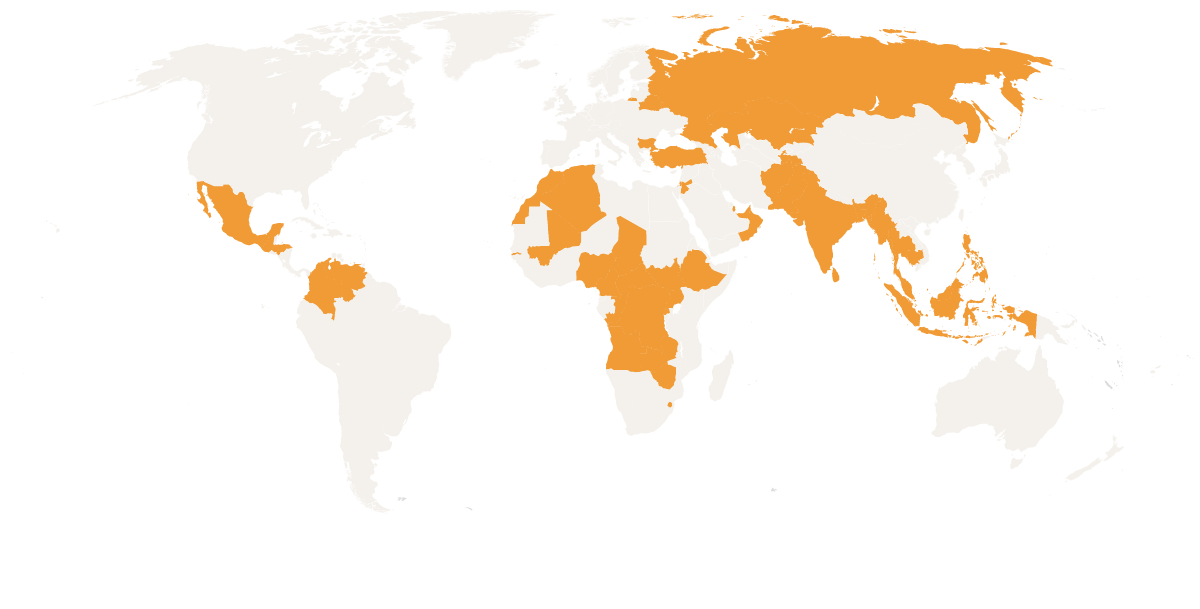
I2P is getting attacked slowing the network and people are beginning to get threatened for circumventing censorship attempts resulting in self-censorship.
- Web: will use I2P with random delays to forward all requests to a 1M5 peer with Tor access at a lower ManCon. If both I2P and Tor blocked at end user, non-internet will be used to find a 1M5 peer at a lower ManCon to fulfill the request.
- P2P: will use I2P with random delays of 4-10 seconds. If I2P gets blocked, will attempt to use Tor as a tunnel. If that is blocked, non-internet will be used.
- Expect latencies of 6-16 seconds unless non-internet used which could result in very large latencies where only asynchronous messaging (e.g. Email) and asynchronous web requests (feeds) are plausible.
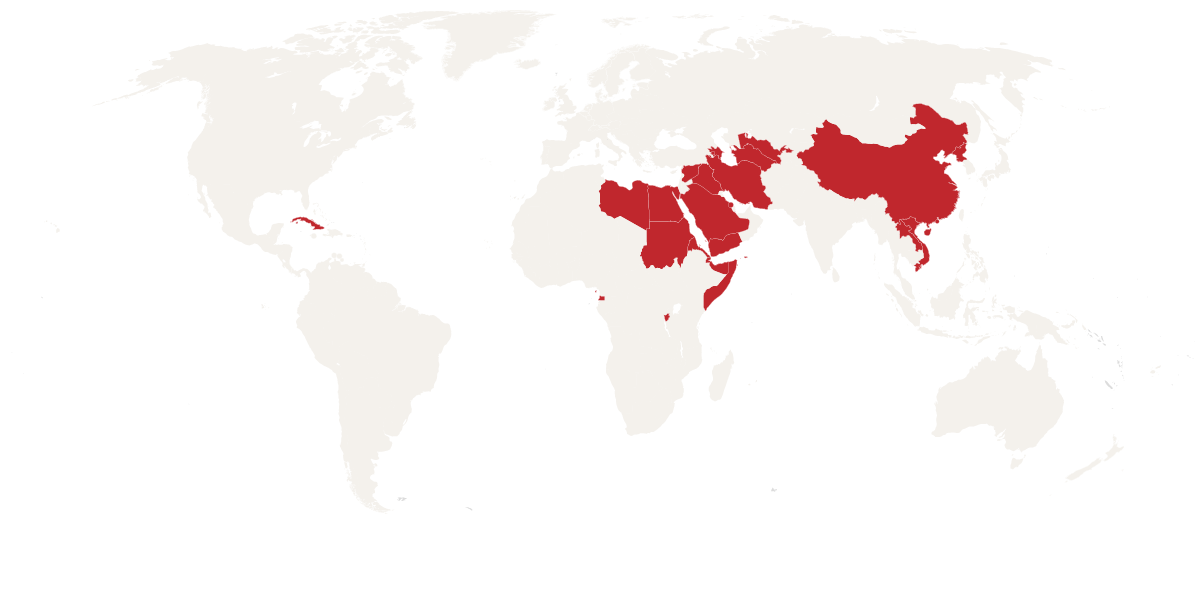
Internet has been blocked for end user, e.g. local cellular service towers shutdown or provider turns off access and/or threats of imprisonment and/or death are made to induce self-censorship with actual evidence of enforcement.
- Web: Non-internet will be used to forward requests to Tor users with a lower ManCon to fulfill the request.
- P2P: Non-internet peers will be used until a peer with I2P access can route the request.
- Expect wide-ranging latencies.
Active sustained censorship of an individual internationally.
- Web: Non-internet is used to forward requests to a peer that will then request another peer using I2P with high delays to make the Tor request.
- P2P: Non-internet is used to forward a message through a random number and combination of non-internet/I2P peers at random delays of up to 90 seconds at the I2P layer and up to 1 hour at the 1M5 layer. A random number of copies (3 min 12 max) of the message are sent out with the end user having a 3/6/12/24 word mnemonic passphrase as the only key to the data.
- Wide-ranging latencies but highest privacy and censorship-resistance.
SUPPORT 1M5
1M5 is an open source project powered by volunteers, bounties and gifts. In the spirit of open source and censorship resistance, we have opted to create 1M5 without the demands or influence of investors.
GitHub
Gift to the 1M5 Development Fund
If you support this mission and are in a position to help that would be wonderful. Please send gifts within the Remnant app.
Gifts to 1M5 are not tax deductible as it is not formally registered in any jurisdiction. By gifting Bitcoin to the 1M5 gift wallet, you will be helping 1M5 pay for our direct costs like web hosting, domain names, outsourced work, bounties, and so on.Get in Touch
Please don’t hesitate to get in touch if you can think of other ways you can help with the 1M5 mission.
PGP: 948E A2E2 C194 AB3C A225 605B 963F 6331 C29F 2342